With data breaches at an alltime high, maintaining a watertight cybersecurity system is at the top of the priority list for most technology companies globally.
However, monitoring and taking precautions with regards to your own cybersecurity just isn’t enough. When working with third party vendors and other businesses, your company data can still become a target for cybercriminals, particularly if their policies aren’t as flawless as yours.
By sending a vendor questionnaire to any potential vendors you plan on working with, you’ll be able to get a better understanding of their security procedures and be able to acknowledge any potential risk factors that come with working with them.
Get our vendor risk management questionnaire template
Content Snare is here to help you create your next vendor risk management questionnaire. Sign up to access our built-in vendor risk management questionnaire template. It’s ready when you are.

What questions should I be asking in a vendor risk assessment questionnaire?
Usually, questionnaire-wise, we strongly recommend shorter rather than longer in terms of length, in order to retain the attention of the individual filling it out.
However, when it comes to internet security, cutting corners just isn’t an option, which is why we’ve provided an extensive list of critical questions below to ensure you cover all of the bases.
Privacy and Security of Information
This section will start to shed some light on how the vendor manages privacy and security and, of course, give you an indication as to whether this vendor’s policies are up to scratch or potentially risky.
- Does your organization process personally identifiable information (PII) or protected health information (PHI)?
- Does your organization have a security program?
- If so, what standards and guidelines does it follow?
- Does your information security and privacy program cover all operations, services and systems that process sensitive data?
- Who is responsible for managing your information security and privacy program?
- What controls do you employ as part of your information security and privacy program?
- Please provide a link to your public information security and/or privacy policy.
- Are there any additional details you would like to provide about your information security and privacy program?
Physical and Data Centre Security
This section focuses deeply on the environmental and physical factors relating to the security of data. That way, you can assess every aspect of the vendor’s situation and identify further possible risks unrelated to the previous section.
- Are you in a shared office?
- Do you review physical and environmental risks?
- Do you have procedures in place for business continuity in the event that your office is inaccessible?
- Do you have a written policy for physical security requirements for your office?
- Is your network equipment physically secured?
- What data center providers do you use, if any?
- How many data centers store sensitive data?
- What countries are data centers located in?
- Are there any additional details you would like to provide about your physical and data center security program?

Web Application Security
The most lengthy by far, this section is a lifesaver when it comes to evaluating the security of the vendor’s web application. These questions will allow you to explore the full spectrum of said application.
- What is the name of your application? And what does it do?
- Do you have a bug bounty program or other way to report vulnerabilities?
- Does your application have a valid SSL certificate to prevent man-in-the-middle attacks?
- Does your application require login credentials?
- How do users get their initial password?
- Do you have minimum password security standards?
- How do you store passwords?
- Do you offer single sign-on (SSO)?
- How can users recover their credentials?
- Does your application employ a defence in depth strategy? If so, what?
- How do you regularly scan CVE for known vulnerabilities?
- How do you do quality assurance?
- Do you employ pentesting?
- Who can we contact for more information related to your web application security?
Infrastructure Security
Finally, all things infrastructure! Learning about the vendor’s infrastructure is the icing on the cake that’ll help you make that final decision as to whether the vendor’s security measures are sufficient or not.
- Do you have a written network security policy?
- Do you use a VPN?
- Do you employ server hardening?
- How do you keep your server operating systems patched?
- Do you log security events?
- What operating systems are used on your servers?
- Do you backup your data?
- How do you store backups?
- Do you test backups?
- Who manages your email infrastructure?
- How do they prevent email spoofing?
- How do you protect employee devices from ransomware and other types of malware?
- What operating systems do employee devices use?
- Are employee devices encrypted?
- Do you employ a third-party to test your infrastructure security?
- Who can we contact in relation to infrastructure security?

What kind of breaches will a vendor assessment questionnaire potentially protect me from?
Yipee! Your vendor risk assessment questionnaire is up, running and ready to be sent to any third party vendors.
However, in order to shed some light on exactly what breaches the questionnaire will help protect you from, let’s go through three of the most common and undesirable internet security breaches that thousands of technology companies are confronted with every year.
Physical breaches
Physical breaches involve losing control over sensitive data directly, often through human error, theft and other various environmental concerns.
Examples of circumstances leading to physical breaches include:
- An employee sending the information to an incorrect recipient
- An insider threat actor sending the trade secrets to competitors
- A robbery occurring inside the organisation’s premises
- An employee leaving a confidential file open on their computer at their desk
- An employee stealing the information to later sell or use in another manner for personal gain
Phishing attacks
A cybercriminal’s end goal is often to access restricted and personal data in an unauthorised manner in order to use said data to threaten people for ransomware. This is commonly achieved through launching phishing attacks to trick employees into clicking on dangerous links and/or downloading malicious resources. Does that ring a bell?
Most people have experienced some type of phishing attack in their lifetime but, with the wealth of knowledge available on the internet about such malicious links and downloads, we know more and more about how to differentiate the fake from the credible. However, on the occasions where the individual does click on any links, the execution of the malware can bypass security controls, allowing access into the system and to unauthorised data.
Password breaches
Newsflash! Passwords can be stolen, lost or guessed a hell of a lot more easily than you would think, especially given the plethora of password breaches that have occurred in the past.There are millions of leaked credentials available on the internet and it doesn’t take much searching to find them.
For this reason, those still relying upon passwords such as ‘Password’ or ‘123456’ are incredibly vulnerable to this type of attack. After having entered an account, the hacker will then be able to steal, alter or delete the desired files and data.
Which tool should I use to create my vendor questionnaire?
After you’ve collated your list of vendor questions,you’ll have to think carefully about which tool you’re going to use to create the assessment questionnaires that are going to be sent to potential vendors. Whilst several seemingly tempting options may surface following a Google search, it’s important to be aware of the many limitations present in the majority of questionnaire and form creation tools.
This is why online tools like Content Snare exist, providing you with a robust range of features whilst remaining simple and straightforward to use.
Content Snare makes it easy to request content and information from anyone, and makes it even easier for vendors to provide their questionnaire responses. Don’t have the time to create a request from scratch? Not a problem - the built-in template library has got you covered.
Sending your first request can take just minutes and, from there, there’s nothing left for you to do except wait for your vendors to start sending in their security details. Anything they type in is automatically saved, meaning that they can return later in their own time, taking away the pressure from everybody, which is particularly important when sending a lengthy and vital questionnaire such as this one.
With its automatic email reminder feature, Content Snare also ensures that vendors continue to make progress until the completion of the questionnaire. Those days of struggling to get the responses and serenity your company’s looking for are well and truly over!
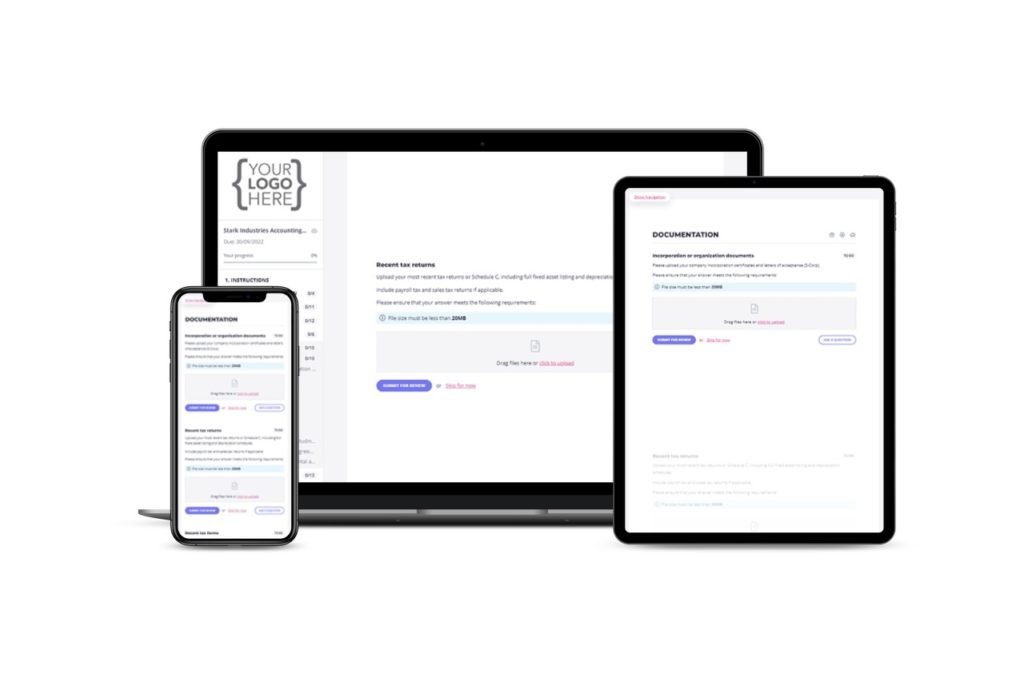
Particularly for those of you with existing or prior security concerns, we really hope that the questions within our vendor questionnaire will be able to give you the peace of mind you need to be able to nip the thought of cyber attacks in the bud.



I would like to get more information about your Vendor Risk Questionnaire please
Hi Maria. Our questionnaire can be viewed on the templates page or inside your Content Snare account after signing up for a trial